In 2023, chief information security officers (CISOs) and directors of identity and access management (IAM) are investing heavily in unified identity solutions with strong security at their core.
They’re making this shift because fragmented identity solutions are no longer capable of securing growing numbers of users, devices, entitlements, and environments—and the increasing costs, risks, and complexity that result from that growth. Identity fulfills multiple use cases across organizations: it prevents security risks, account takeovers, and security breaches with multi-factor authentication (MFA). It provides better user experience with directory and single sign-on (SSO) capabilities that facilitate easier access management. Identity can provide secure access across an IT estate, including mobile devices and cloud applications and accelerate digital transformation.
This trend toward unified identity platform solutions marks an adjustment from the pattern over the last three years focusing on remote employee strong authentication and extends security across all identity components. CISOs, security experts, and IT teams claim that they face dramatic shifts in culture and security as work-from-home gives way to return-to-office, all while employees turn coat and change jobs on a dime. Those shifts mean that every user’s credentials are a pathway to devastating data breaches—every user is a privileged access user.
Vendors like Microsoft and investment firms like Thoma Bravo have responded by rapidly adding access management, directory services, passwordless authentication, and other identity functionality to their respective portfolios. However, CISOs interviewed for this report are, with few exceptions, looking to security-focused vendors to prevent security identity-based attacks, detect security threats, and produce a unified, security-focused identity platform, fabric, or experience.
Impact Leaders, on behalf of RSA Security, interviewed at length 25 executives in large enterprises on their spending plans for 2023 and their perceptions of identity strategy, digital transformation, the access management space, identity-based attacks, technologies, and trends.
Furthermore, in January 2023, Impact Leaders consulted by telephone six senior executives at large firms with average revenues of US$40bn for relevant quotes and insights on their views of unified, security-focused, identity.
CISOs view a single security-centered vendor as the right identity partner for the future. Impact Leaders’ research shows that CISOs have strong opinions about why identity is their focus now, why a unified experience matters, and why a security focus by their preferred identity providers is paramount.
IT executives feel pressure to extend data protection from simple security perimeter defense to defense-in-depth. With remote work, identity has become arguably the furthest extension of that concept: it is the new perimeter as employees work from home, co-working spaces, coffee shops, and other public places.
According to the 2022 Verizon Data Breach Investigations Report (DBIR), 82% of breaches involved the use of stolen credentials, phishing, and other human-related vulnerabilities as the starting point for security breaches.1
No organization is safe without a plan to handle security risks like credentials, phishing, account takeovers, and other vulnerabilities securely.2 The DBIR also showed that criminals are growing their exploitation of user credentials at a rate to match the last five years combined.3
Whether an organization is just dipping a toe in the “strong authentication” pond or revamping access control to support a sudden shift to a remote workforce, Identity represents more than just another security project. It is the most accurate barometer of the overall health of a risk management program.
100% of CISOs and technology leaders surveyed value cost-effectiveness over cost alone.
When a company is growing—organically or by acquisition—it can rely on identity to ease integrations of acquired companies, integrate cloud services, and to help entering employees to have an easier transition and faster time to full productivity. It also helps with layoffs; deprovisioning is easier because it can be automated. In short, identity is the foundation of technical risk management.
IT and security executives interviewed for this report detailed their strategies for enrolling support for unified, security-focused identity. They said they get more budget, more headcount, and more enduring support from senior management for identity initiatives by keeping a laser focus on value at both the top and bottom of a balance sheet. The bottom line shows the value of costs avoided, like risk reduction, downsizing, regulatory compliance, preventing security breaches, and so forth, while the top line shows the value of benefits received, like revenue, new business, renewal rates, improved user experiences etc. Unified, security focused identity tracks on both the top and bottom lines of the balance sheet in four themes (Figure 1).
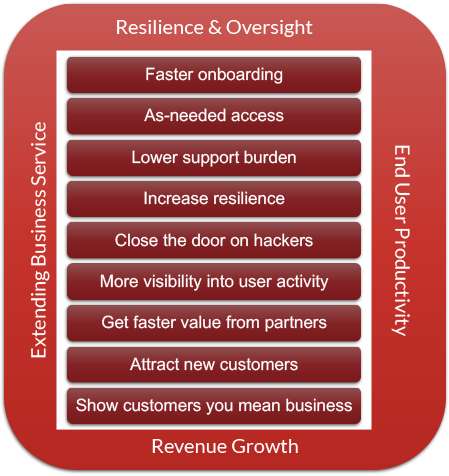
Figure 1: Business drivers for identity solutions
Source: Impact Leaders
More than half of CISOs reported the “most aggravating” aspect of identity is working with four or more identity vendors. Two-thirds of CISOs prefer having one or two identity providers rather than multiple vendors.
While only a few CISOs (less than 10%) think that a decade from now the cybersecurity market will consolidate to a handful of big providers, like Microsoft, Palo Alto Networks, Amazon, and Thoma Bravo, that is simply unlikely.
Consolidation in the security industry has been tried dozens of times over the last forty years and it just does not work.
Large cloud resources providers are scrambling today to build out product portfolios and to integrate in a few years what organizations have spent decades fine-tuning in their own data centers.
The rush to be “all things IT” by these big providers creates a natural resistance in enterprise adoption, because large cloud providers will not keep up with fast-moving business dynamics or address rapidly-evolving security risks. Moreover, large corporations will not put all their eggs in one cloud services provider, according to Impact Leaders research.
Large cloud providers do not focus on security. They may take it seriously, but that is different than making it their raison d’etre. Today and for years to come, CISOs plan to use specialized vendors to tackle the biggest slices of the IT security pie: security risks, identity-based attacks, identity and access are slices that CISOs and IT Teams want to take care of in one bite.
72% of IT executives say security is the primary factor when choosing an identity provider.
CISOs seeking identity solutions today want a vendor partner they can count on, one that integrates the entire identity infrastructure and lifecycle, and one that reflects best practices from security experts:
“Windows can’t be our sole security partner. It just doesn’t do enough to secure and integrate with our fragmented environment and hundreds of downstream apps.”
–CISO, $30BN CONSUMER PRODUCTS COMPANY
One CISO said this when asked why they preferred a unified product portfolio from a security-focused provider:
“Our employees often don’t have smart phones at work, yet we still need high security across every part of our identity and access footprint. I have high hopes for passwordless multi-factor authentication (MFA) in the future, but today I need a partner who can get identity done, get it working, and keep it secure.”
–EXECUTIVE, FORTUNE 500 CHIP MANUFACTURER
One national credit union received, according to its CIO, US$2.9M in net benefits to infrastructure and risk over a two-year period by deploying a unified, security-focused identity solution:
“We heard horror stories from peers at other credit unions, and from local companies in healthcare, who have been attacked and had to pay ransoms in bitcoin or be out of service for days or weeks while restoring operations. We knew for us it was just matter of time until we got hit.”
-EXECUTIVE, NATIONAL CREDIT UNION
84% of respondents want security solutions to integrate with Microsoft, while 92% do not want to rely entirely on Microsoft security.
Microsoft is an incumbent and respected provider of on-premises infrastructure in most large enterprises. Microsoft is also a respected cloud services provider with Microsoft Azure Active Directory and a growing portfolio of cloud apps.
The challenge CISOs face is that Microsoft does not offer the same products with the same functionality to both cloud environments and on-premises resources. It is essentially two portfolios of products that cannot duplicate performance in their respective deployments.
Every credential is a target to sophisticated criminals; therefore every user should be treated as having privileged access.
CISOs prefer unifying identity instead of having one or two providers. A unified, security-focused identity provider produces measurable benefits in both developing a stronger security system, preventing risks, and enhancing user experience.
Identity is the aspect of IT infrastructure that has the greatest impact on an organization’s risk. Security focus is the primary factor used in selecting an identity provider.
This article is based on the original Impact Leaders report. View the original report here.



