Transform zero trust from an idea into a reality
Zero trust isn’t a particular technology or service. It’s a different way of thinking about security. The idea behind zero trust is that you can’t assume someone or something can be trusted, even within the network perimeter. With the zero-trust model, everyone is considered a potential threat, and every interaction is a potential risk. Before someone is given access to a resource, they need to be verified first.
But how do you go from abstract concept to practical security strategy? You start with identity.
Establish the right level of trust
Zero trust is about establishing the right level of trust before granting access. Identity is central to zero trust, and RSA offers a range of multi-factor authentication (MFA) methods as well as governance and lifecycle capabilities to enable governance-based access authorization.
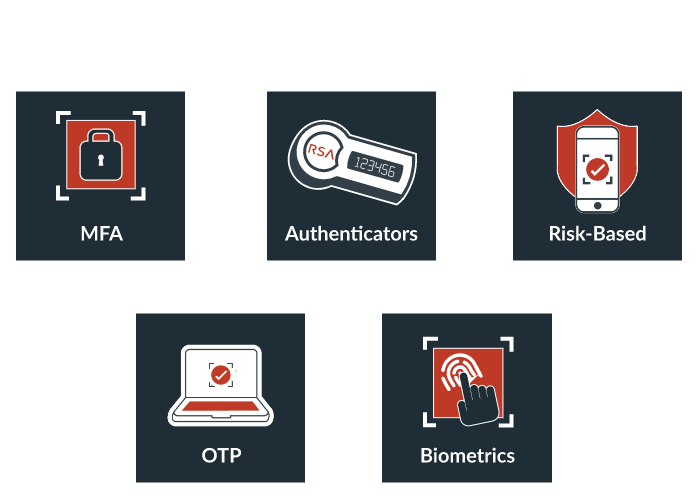
Enable dynamic decision-making
To determine the level of risk, you need to understand the context for an access request. RSA risk-based authentication technology enables the dynamic decision-making required to establish trust continuously. Behavioral analytics, anomaly detection, and related technologies help uncover relevant context for access attempts.
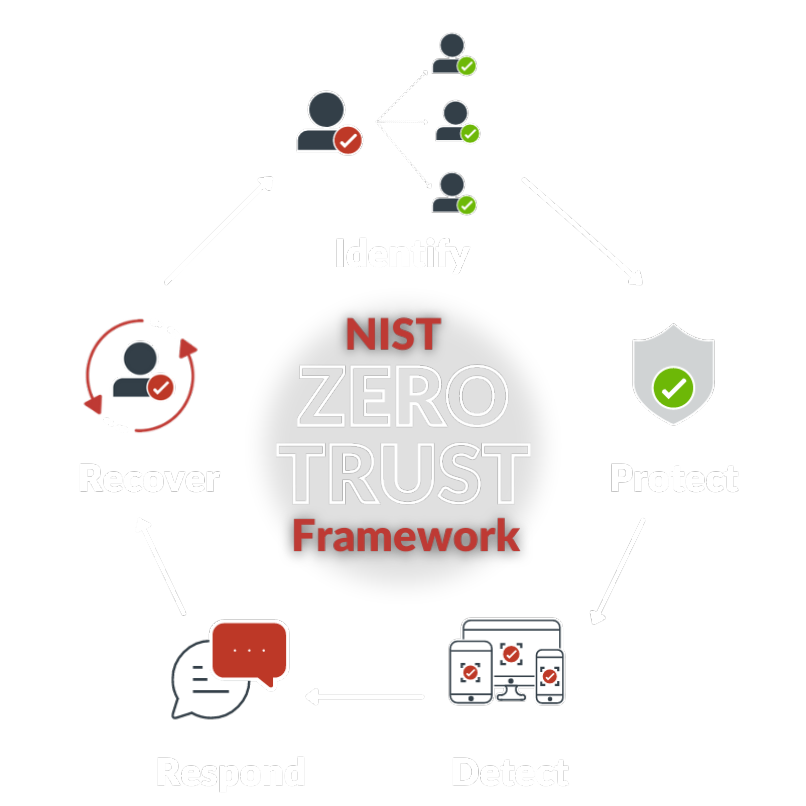
Align with the NIST framework
NIST has defined an architectural framework to support key tenets of zero trust. RSA provides the identity and access management (IAM) components that are fundamental to working within the NIST framework, including MFA, identity governance and lifecycle, risk-based analytics, and role- and attribute-based access.