Why Leaders Prioritize Identity
Without a unified identity solution, organizations pay more for weaker security.
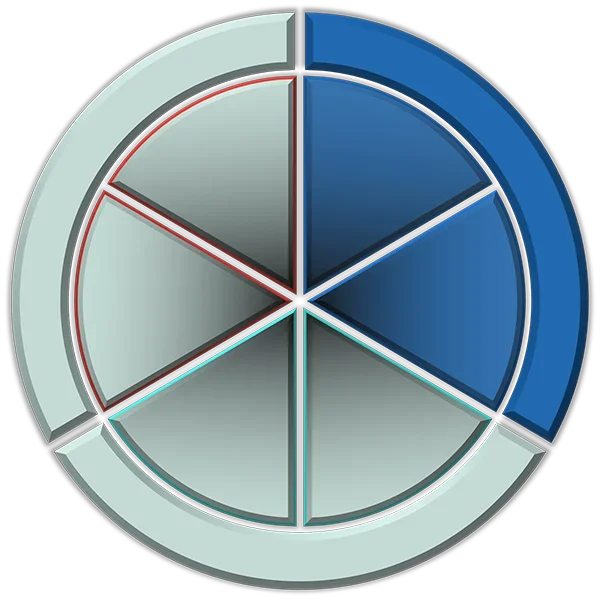
72%
of IT executives say security is the primary factor when choosing an IAM provider.
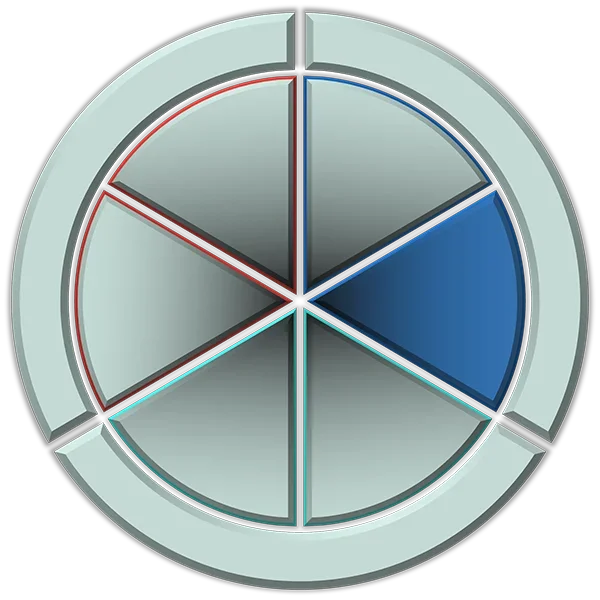
82%
of breaches involved the use of stolen credentials, phishing, and other human-related vulnerabilities.
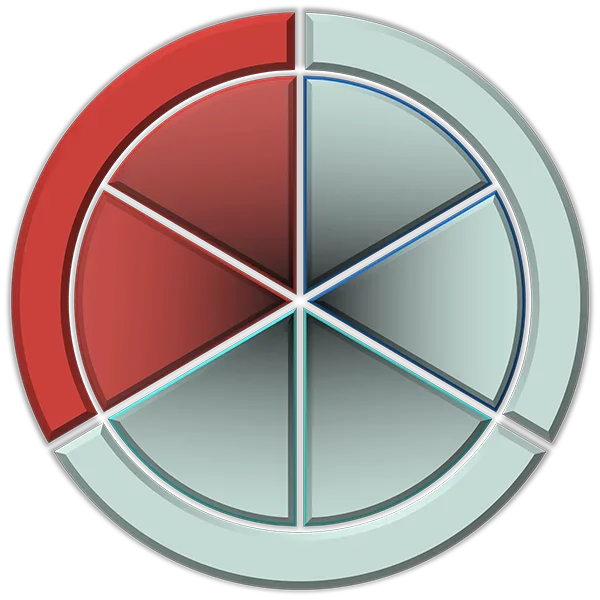
100%
of CISOs and tech leaders value cost-effectiveness over cost alone.
Benefits of a Unified Identity Platform
Organizations using a unified identity platform can realize significant benefits. Organizations can extend these benefits by ensuring that their identity platform can support their environment today and scale over time to support future cloud investments.
- Reduced risk of human error in managing entitlements
- Improved operational efficiencies for credential management
- Lower costs with automation

S
e
c
u
r
e
A
c
c
e
s
s
Stop advanced identity attacks
Prevent help desk fraud
S
t
r
e
n
g
t
h
e
n
P
o
s
t
u
r
e
Automate identity lifecycle to reduce risks
Streamline identity governance & compliance
G
o
P
a
s
s
w
o
r
d
l
e
s
s
Build MFA resilience with cloud/hybrid
Stop phishing
RSA Unified Identity Platform
Automated Identity Intelligence
- AI-powered adaptive authentication policies
- Mobile threat detection
- Dashboards, reports, and insights
Authentication
- Advanced MFA
- Support for software and hardware authenticators
- Phishing-resistant hardware tokens
Access
- Secure, simplified access management
- Self-service capabilities
- Unified Directory
Governance & Lifecycle
- End-to-end visibility
- Audit and compliance readiness
- Visualizations into entitlements
Products
Identity-First Products for Security-First Leaders
ID Plus
A complete, secure identity platform providing multi-factor authentication (MFA), access, single sign-on (SSO), directory, and additional capabilities for all users across cloud, hybrid, and on-premises environments.
Learn More
SecurID
On-premises products that balance rigorous security and convenient authentication across use cases.
Learn More
Governance & Lifecycle
Reduce the identity attack surface, maintain compliance, and manage access throughout the user lifecycle.
Learn More
Connect with RSA.
Contact RSA to learn more about our products.